Perils of Power V
In order to rise to the dizzying challenge of safeguarding American energy infrastructure, several actions must be acted upon promptly.
To begin with the most granular prescriptions, cybersecurity professionals within energy companies must work in tandem with COOs to implement robust “cyber hygiene”. This entails running stress-tests, health-checks and internal audits of company IT and OT. Simply orchestrating mass-software updates and reminding all employees to update their applications, from their browser to their entire operating system, is a relatively small task that can prevent potentially devastating consequences. This is commonly referred to as “Patch & Configuration Management”. “Patch Tuesday'' has become an often frivolous term in the cyber vernacular, but it propounds a sensible message – it is often when digital behemoths like Microsoft, Adobe, Google, and others release patches to zero-day or known vulnerabilities in their operating systems. Enforcing and rewarding company-wide patch management should be a priority, because malware doesn’t care about hierarchy. The CEO’s desktop can be as vulnerable as the entry-level analyst’s. But the CEO’s may be the more coveted target.
What’s also illuminating in this field is that the most simple of actions can be the most foundationally secure. Granted, tomorrow’s cyber belligerents may find ways to evade basic security controls, and the implementation and improvement of controls is a constant endeavor. But if COOs and CTOs at companies make two-factor authentication, non-repeated passwords, biometric identification processes, and cyber-literacy training mandatory, internal and external market operational confidence can be further guaranteed. Simultaneously, access to various components of the IT/OT should be placed in the hands of only a few dedicated employees, all of whom would receive guidance on their specific roles to play in protecting the supply or value chain. This curtails sclerotic bureaucracy in investigating who-runs-what.
Furthermore, designated cybersecurity professionals ought to maintain an entire inventory of every single facet of their digital being. All hardware, software, firmware, applications installed, browser extensions, company-issued mobile devices - every single piece of technology adopted by the company should be documented in a cohesive inventory list to avoid confusion and bolster mastery of the entire value chain. Employees should view the technological tools that empower them as being efficient and streamlined, not nebulous and overwhelming.
This is all the more integral based on the following chart in Figure 8, which aggregates survey data from a GlobalData-EnergyMonitor questionnaire sent to employees within certain sectors. On average, only 31% of respondents could confidently say they knew how to respond to a potential cyberattack. This is a paltry figure. But when their employers are not making resources mandatory or ubiquitous, can they really be blamed?
Figure 10. Results from a DNV.com survey from July 2022, published on EnergyMonitor.io.
One of the most perilous threats to any organization is one far more nefarious than any nation-state or malware code: you. Insider threats refer to the notion that an internal employee at a company may be the precipitating factor for a massive cyber disruption, either through negligence or lack of education within cyberspace. The term to many invokes facetious images of clicking on a typo-laden email link, or downloading what purports to be a key set of materials for their 11AM meeting. But insider threats represent a formidable threat to organizations: The Ponemon Institute’s 2022 Cost of Insider Threat report reveals that cyber incidents derived from insider threats has risen 44%; the cost per incident has increased by more than a third to $15.38 million. This pales in comparison to the cost of implementing cybersecurity controls – many enterprise-wide encryption solutions are in the region of two thousand dollars. CISA provides a fantastic framework for insider threat management that should be easily accessible and a contingent of new-employee onboarding. It entails “Defining, Detecting, Assessing, and Managing” insider threats. The framework helps establish a standard vocabulary and aims to diffuse a culture of transparency, reporting and accountability; this in turn aims to absolve the notion of shame or embarrassment in not knowing how to act in a particularly sensitive cyber situation. It is not particularly difficult to provide quick visual guides on how to ensure best practices, particularly when agencies like CISA and the DOE publish countless completely free resources and infographic posters to display in the workplace. Figure 9 is an example of a ransomware prevention poster that ought to be as predominant in workplaces as choking hazard notices are in restaurants. They could potentially save companies millions of dollars, and stave off cyber adversaries that persistently attempt to compromise a certain company.
Figure 11, A sample poster from CISA on Ransomware.
Simulations, security controls, and educational resources are all positively prescient tools that are meant to be in place before and during a cyber onslaught from a threat actor. What frameworks can be used by energy infrastructure staff amidst a cyber disruption or attack? In order to heighten proficiency of the operational atmosphere, cybersecurity professionals need to espouse one of the leading resources that bombastically enjoys thinking like the adversary. The MITRE ATT&CK framework, displayed below in Figure 10, has been advocated as being industry standard and rightly so. MITRE’s Adversarial Tactics, Techniques and Common Knowledge framework empowers a wide range of stakeholders to gain insight on the lifecycle of a cybersecurity incident. Cybersecurity firms are unanimous in championing MITRE’s models for providing a “curated knowledge base and model for cyber adversary behavior…reflecting various phases of an adversary’s lifecycle”. Consulting the MITRE framework in the heat of a cyber disruption allows company cyber personnel to stay one step ahead of the technical lifecycle. These officers can also utilize the framework to retroactively understand when and where the critical vulnerabilities lay within their organization. As evinced by personnel confidence indicators and the behavior of Colonial’s employees during DarkSide’s breach, experiencing a cyber incident can be an extremely disturbing, panic-inducing experience that no employee would ever wish to endure. In MITRE essentially mapping the disruption life-cycle, an organization has a resource to congregate around in times of a cyber calamity.
MITRE ATT&CK Framework, 2022.
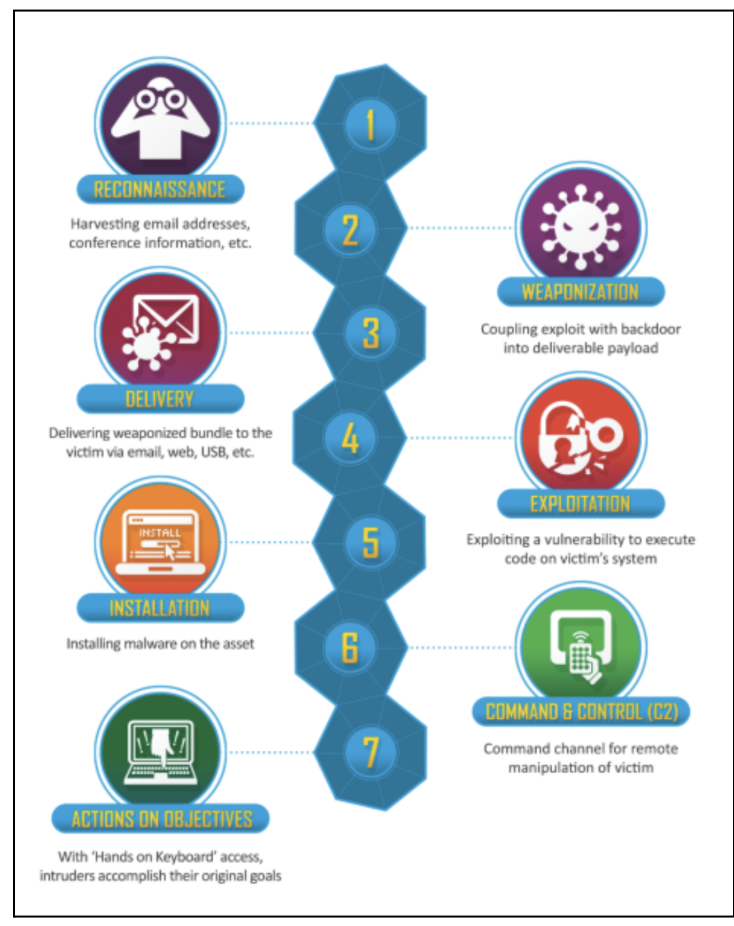
Lockheed Martin’s Cyber Kill Chain in Figure 11 is another praiseworthy alternative; it is slightly simpler and therefore perhaps more easily didactic; however it is devoid of the intense level of detail abundant in the MITRE framework.
Yet, its creation is unequivocally applauded by this author, for the simple reason that it introduces another massively consequential relationship: the rapport between the public and private sectors.
The U.S.’s significant advantage in the global cyber hierarchy is the presence of an intellectual and digital nucleus that is far and away the finest in modern history. Concurrent with the country’s rise as an unparalleled superpower throughout the 20th century, the late 1990s bore witness to the efflorescence of a dot com private sector that has arguably replaced financial companies as the titans of industry. Alphabet, Meta, Amazon, Microsoft, Oracle, Nvidia, Intel, and Dell are but a few of the most powerful, advanced entities in the history of our digital being. It should furthermore give the nation comfort that the two most trailblazing, revolutionary artificial intelligence large language model platforms in ChatGPT and Bard are being developed by two American giants in Microsoft and Alphabet’s Google respectively. All of this is to say that public-private partnerships must become commonplace in the effort to successfully defend the U.S. against perilous perpetrators. Palo Alto Networks, Coalfire, Rapid7, and Mandiant should become household names for any professional working with an interconnected device within the energy industry.
In what must be hailed as a positive step, President Joseph R. Biden’s National Cybersecurity Strategy for 2023 released at the beginning of March repeatedly stressed the importance and need for public-private collaboration within the processes of safeguarding American critical infrastructure. In this proclamation, Biden’s administration correctly identified that these colosses of industry are the only ones capable to develop the “speed and scale” of defense apposite for the threats of tomorrow. The legislative chambers of federal and state Houses have also become swift to act, intriguingly at a faster rate since a certain pipeline ceased their operations in May of 2021. According to the EnerKnol Platform’s proprietary Search engine, which consolidates every energy-oriented regulatory and judicial filing across the U.S., there are 128 matches for either pending or enacted legislation with the term “cybersecurity” in the title of the bill. This revolutionary sweep of codification will serve the country well in becoming home to an unmistakably powerful hub of cybersecurity expertise, and the public-private spread of education with regards to how to control, and not be subjugated by, the omniscient cyber domain will act as a national security bulwark for several generations henceforth in an increasingly volatile world.